Description:
HellMath – Mongolia – 100 – PPC – NEW
EN: Somebody thinks that you are able to calculate well. Is it true? Pass this task, prove the abilities and maybe we will recommend you to one of the most secret missions in this war.
# nc ctf.com.ua 9988 #
This one was a tricky question. Sometime we tend to think too complicated that we forget the basics of the basics.
Let’s begin. We are given with a netcat command. Let’s run it and see what will happen:
Megabeets: /tmp/h4ck1t/# nc ctf.com.ua 9988 Hello, stranger! In this task you must solve 100 math questions. Every task prints value C, where C = A ^ B and you need to return A and B. Simple, isn't it? C = 902688766290655704373689275053375955411443638316509920323848941975222889419457168696920458154297992623673837270038581569454814243805830583810239007096636651566143112784253577358992076929281284042240081518611899927486014041391480636127371844583712500925858241436577687881647483088199415935267570657867465207599620844695004309619118983781089160978919651087719815749856394166367766706778110070467678821838496167634418163901082752730509337302890389749997313424181834067339889277882795763685153563883836605864618300712713269080489519361527692457350059854544553090827217232806958474200121801180519077734723322730821821456307012680580248247037218481409333193782453105202353618778481032198022578852166518606909721942977575590954265237839696664727220865292977163448587698573864445402565395985502519681641780784380764161304054798829812233490916257278759562538568573426337720533085242758348167474155869479478584700074966635983754095730722241717146186660268605302301836193395575194171496181059843678720055443249024604241326634039569309251564445571858850712209536694524027635248909838940066204355066967778407959555544148932174508982884171285719680370353907943024211899094303816973257264835368157414233144693065775543775665646374894255716733398422962657186374363379853482641303616490385754787152837430574499189926206208167378653776600678668050752826349915972573133077173212387799225263508329369454811848100118727431542734051975488119495581578101088438806260901755298558179381970655381433179960687477909164284017317873303284836205753800005799794061481880410000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000
Well, We are given with a number C and we need to find numbers A and B that A^B (Power, not XOR) gives C.
At the beginning I tried to find algorithms online, “Such algorithms must exist!” I thought to myself. I found nothing and gave up for the day because it was late and I wanted to sleep. I was in my bed while message a friend the question and he simply answered:
“Did you tried 1?”
– “What 1?”
“You know, every number power 1 equals the number” (i.e C = C^1)
– “OMG! It is so simple! You are the smartest person on earth!”
So I ran to my computer and wrote this short python script that gave me the flag:
from pwn import *
from time import sleep
r = remote('ctf.com.ua', 9988)
print r.recvuntil('?')
print r.recvline()
counter=0
while True:
if counter==100:
print r.recv()
q = r.recvline()
c = q[5:].rstrip('\n')
print q
print "\n----------\n"
print c
ans = '%s 1'%c
print ans
r.send('%s\n'%ans)
counter+=1
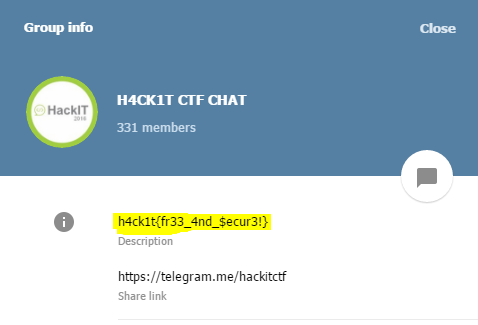
# Flag: h4ck1t{R4ND0M_1S_MY_F4V0UR1T3_W34P0N}
Flag: h4ck1t{R4ND0M_1S_MY_F4V0UR1T3_W34P0N}