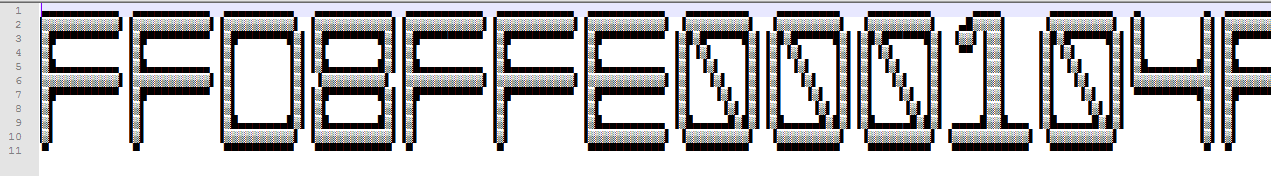Description:
ch17ch47 – Germany – 200 – Forensics
Find out who is the recipient of the information from the agent.
http://ctf.com.ua/data/attachments/CorpUser.zip
This challenge was second in this CTF which took me no more then five simple and basic commands in order to get the flag.
I roughly follow the same simple system whenever I face a new challenge. This system has prove itself again and again in almost any kind of challenge in different levels.
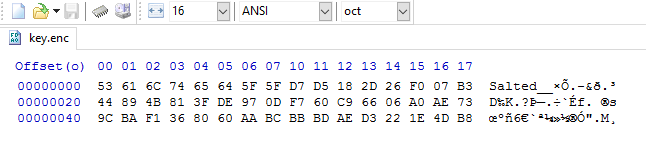
- Examine the file types that are given to you: An image, pcap, pe, etc. You can do it using the
filecommand or just by open it - Run ‘strings’ command on it.
strings file_name | grep - i flag{convention} - Run foremost (and binwalk) on the file
- Run
stringson all the extracted files
Megabeets:/tmp/h4ckit/germany# unzip CorpUser.zip Archive: CorpUser.zip creating: CorpUser/ creating: CorpUser/AppData/ creating: CorpUser/AppData/Local/ creating: CorpUser/AppData/Local/Apps/ creating: CorpUser/AppData/Local/Apps/2.0/ creating: CorpUser/AppData/Local/Apps/2.0/2VQLGYNY.ZHM/ creating: CorpUser/AppData/Local/Apps/2.0/2VQLGYNY.ZHM/X90XE08W.MG4/ creating: CorpUser/AppData/Local/Apps/2.0/2VQLGYNY.ZHM/X90XE08W.MG4/clic...exe_baa8013a79450f71_0001.0003_none_8554920337a51673/ inflating: CorpUser/AppData/Local/Apps/2.0/2VQLGYNY.ZHM/X90XE08W.MG4/clic...exe_baa8013a79450f71_0001.0003_none_8554920337a51673/GoogleUpdateSetup.exe creating: CorpUser/AppData/Local/Apps/2.0/2VQLGYNY.ZHM/X90XE08W.MG4/google.app_baa8013a79450f71_0001.0003_75c9b16f02ab5371/ inflating: CorpUser/AppData/Local/Apps/2.0/2VQLGYNY.ZHM/X90XE08W.MG4/google.app_baa8013a79450f71_0001.0003_75c9b16f02ab5371/GoogleUpdateSetup.exe inflating: CorpUser/AppData/Local/Apps/2.0/2VQLGYNY.ZHM/X90XE08W.MG4/google.app_baa8013a79450f71_0001.0003_75c9b16f02ab5371/clickonce_bootstrap.exe inflating: CorpUser/AppData/Local/Apps/2.0/2VQLGYNY.ZHM/X90XE08W.MG4/google.app_baa8013a79450f71_0001.0003_75c9b16f02ab5371/clickonce_bootstrap.exe.cdf-ms inflating: CorpUser/AppData/Local/Apps/2.0/2VQLGYNY.ZHM/X90XE08W.MG4/google.app_baa8013a79450f71_0001.0003_75c9b16f02ab5371/clickonce_bootstrap.exe.manifest inflating: CorpUser/AppData/Local/Apps/2.0/2VQLGYNY.ZHM/X90XE08W.MG4/google.app_baa8013a79450f71_0001.0003_75c9b16f02ab5371/clickonce_bootstrap_unsigned.cdf-ms inflating: CorpUser/AppData/Local/Apps/2.0/2VQLGYNY.ZHM/X90XE08W.MG4/google.app_baa8013a79450f71_0001.0003_75c9b16f02ab5371/clickonce_bootstrap_unsigned.manifest creating: CorpUser/AppData/Local/Apps/2.0/2VQLGYNY.ZHM/X90XE08W.MG4/manifests/ inflating: CorpUser/AppData/Local/Apps/2.0/2VQLGYNY.ZHM/X90XE08W.MG4/manifests/clic...exe_baa8013a79450f71_0001.0003_none_8554920337a51673.cdf-ms inflating: CorpUser/AppData/Local/Apps/2.0/2VQLGYNY.ZHM/X90XE08W.MG4/manifests/clic...exe_baa8013a79450f71_0001.0003_none_8554920337a51673.manifest ... ... DELETED LOT OF ROWS ... ...
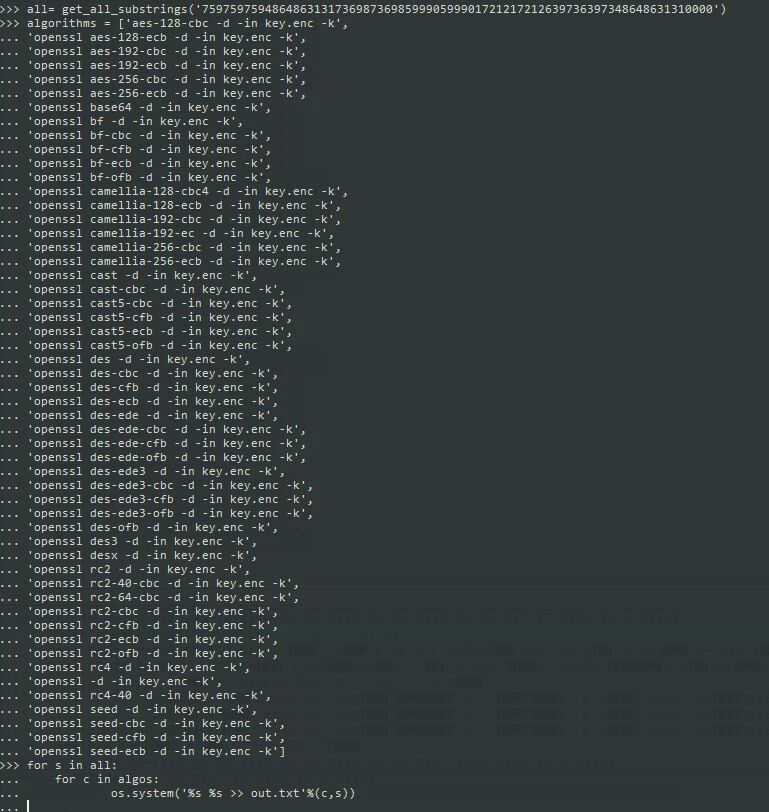
We have a lot of files of different types from what seems like Windows machine (AppData, Favorites, Downloads, Desktop…). We can start step 2 that I mentioned before and recursively search for the flag in the strings of the files.
Megabeets:/tmp/h4ckit/germany# grep -R 'h4ck' CorpUser Binary file CorpUser/AppData/Roaming/Skype/live#3aames.aldrich/main.db matches
This command iterates recursively all the files in the directory and the sub-directories and grep for the string ‘h4ck’. The command returned that there is a database file that is containing part of the flag. Now let’s strings command on the file:
Megabeets:/tmp/h4ckit/germany# strings CorpUser/AppData/Roaming/Skype/live#3aames.aldrich/main.db | grep h4ck1t
live:black.zogzog blackabauh4ck1t{87e2bc9573392d5f4458393375328cf2}h4ck1t{87e2bc9573392d5f4458393375328cf2}8183ce2902ef71ac62ab02a7c8ec762e6b14e318h4ck1t{87e2bc9573392d5f4458393375328cf2}h4ck1t{87e2bc9573392d5f4458393375328cf2}h4ck1t{87e2bc9573392d5f4458393375328cf2}h4ck1t{87e2bc9573392d5f4458393375328cf2}
And we got the flag. Easy, right?
Flag: h4ck1t{87e2bc9573392d5f4458393375328cf2}