Description:
v01c3_0f_7h3_fu7ur3 – Australia – 300 – Network
The captured data contains encrypted information. Decrypt it.
http://ctf.com.ua/data/attachments/wireshark_8764d640d217fd346e2db2b5c38dde13.pcap
The first thing I do when I face a pcap challenge is, of course, open it in Wireshark. If it looks normal (and not, for example, Bluetooth traffic) I then run ‘foremost‘ on the file. ‘foremost‘ is searching for a known files in a given file by file headers, footers etc, and then extract it to ‘output’ folder in the directory.
So foremost found several files in the PCAP from several sources like http and ftp traffic
- png
- gif
- jpg
- rar
- (…)
I opened the rar archive and found a file named ‘key.enc’ which contained “Salted_<GIBBERISH>” . I opened it in hex editor:
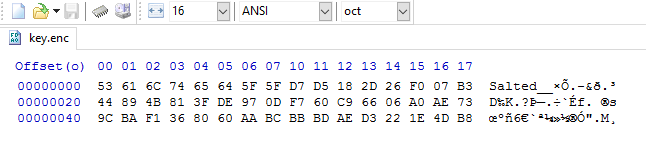
At the first, as the name says, I thought I found the key of some encryption and now I need to find the encrypted file and the cipher. But in a second thought I said to myself that ‘*.enc’ is usually for the encrypted files! So that file isn’t a key, it’s encrypted and we need to decrypt it. But what is the key and the cipher?
So, I figured out that file that starting with “Salted_” is file that was encrypted using ‘openssl’ application.
I then went to read the task again, I saw that the name of the challenge is “v01c3_0f_7h3_fu7ur3” so I thought maybe it involves some audio. Searched for ‘mp3’ or ‘aud’ in the pcap (queries: ‘tcp contains mp3’ , ‘tcp contains aud’) and found the following url:
http://priyom.org/scripts/audioplayer.min.js
It’s an innocent javascript file. I entered the “priyom” site and read it’s description:
“Priyom is an international organization intending to research and bring to light the mysterious reality of intelligence, military and diplomatic communication via shortwave radio: number stations”
Sounds interesting. So I looked up again in the pcap and saw a request to this specific url:
http://priyom.org/number-stations/english/e06
There is a robotic voice that reads out numbers.
75975975948648631317369873698599905999017212172126397363973486486313100000
So I now have what seems like a key, so what is the encryption?
A bit research about the encryption made me think it’s AES so I ran:
openssl aes-256-cbc -d -in key.enc -k <the long key>
-d is for decrypt
-k is for keyphrase
Failed. So I read about the structure of the voice record in the website and took only the Message part from the numbers: 7369859990172126397300000
this is the actual Message part (5-digit paired groups) and 5 zeroes at the end. without the Intro, Outro, Premable, Postmable and the Duplicate 5-digits.
Failed again. Tried it with all the possible openssl encryptions (20+) but failed again.
So I got mad and tried to decrypt it using all possible encryptions with all possible substrings of the original number from the record.
Pseudo code:
for sb in all_possible_substrings(key)
{
for enc in all_possible_encryptions:
(
openssl encr -d -in key.enc -k sb
)
}
And how it was really looks like:
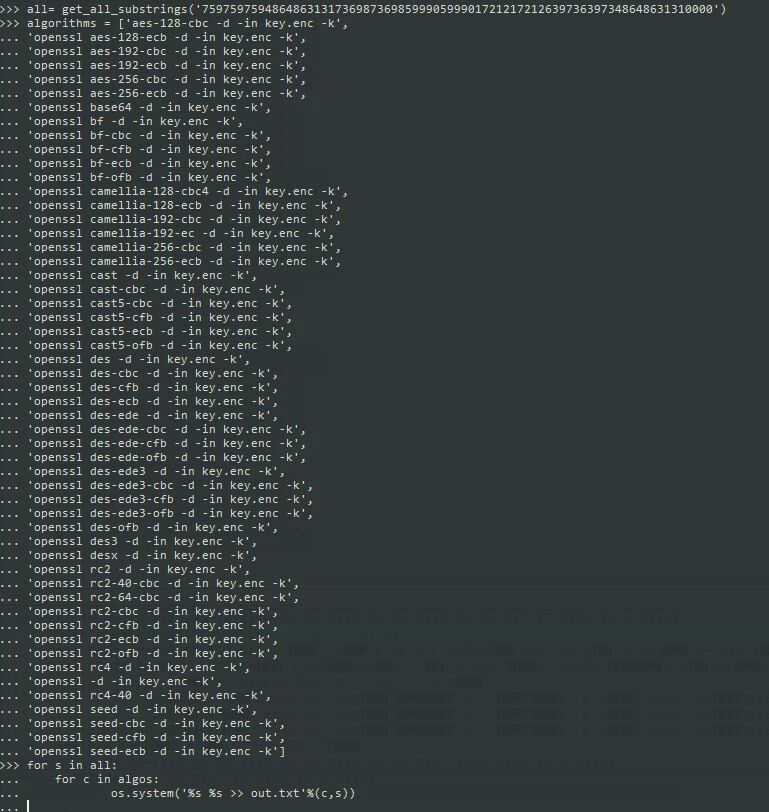
it took 30 minutes to run.
BUT FAILED. No flag.
At this point I think that 3 or 4 teams already solved it.
So I tried more and more combinations and this stupid one finally worked:
Megabeets:/tmp/h4ckit/australia# openssl aes-256-cbc -d -in key.enc -k 75948631736985999017212639734863100000
h4ck1t{Nic3_7ry}
It’s the full number from the recording but delete the duplicates pairs (the recording was splitted to group of numbers and the speaker said each group twice or three times).
So the hardest part was actually to figure out the exact keyphrase, the rest was pretty easy.
Flag: h4ck1t{Nic3_7ry}
