Prologue
A month ago in Barcelona I was attending to r2con for the first time. This is the official congress of the radare2 community where everyone can learn more about radare2 framework and dive deep into different aspects of reverse engineering, malware analysis, fuzzing, exploiting and more. It also the place where all of us, the contributors and developers of radare2, can meet, discuss and argue about every other line of code in the framework.
This was the second congress of radare2, after the success of the first congress in last year which was also a celebration for radare’s 10 years old birthday. This year the conference was bigger, fancier and probably organized much better. r2con was four days long, starting at September 6 and lasted until September 9. The first two days were dedicated to training and took place at Universitat de Barcelona. The other two days were talks days and took place at the MediaPro.
Crackmes Competition
During r2con this year there was a Crackmes competition where all the attendees were given with the same 5 challenges and had to publish a writeups to all the challenges they had solved. The scoring was based on the quality of the writeups along with the quantity of solved challenges.
I won the competition and got myself some cool swag!
- Flag of radare2
- POC | GTFO book
- Orange PI with 3D printed case of r2con logo
- Radare2 stickers
- A beer 🍺
I thought of sharing some of my writeups with you, so you can taste a bit from what we had in the competition and so that others, coming from google, twitter and such, could learn how to use radare2 for solving different challenges. This article is aimed to those of you who are familiar with radare2. If you are not, I suggest you to start from part 1 of my series “A Journy Into Radare2”.
Getting radare2
Installation
Radare2’s development is pretty quick – the project evolves every day, therefore it’s recommended to use the current git version over the stable one. Sometimes the stable version is less stable than the current git version!
$ git clone https://github.com/radare/radare2.git $ cd radare2 $ ./sys/install.sh
If you don’t want to install the git version or you want the binaries for another machine (Windows, OS X, iOS, etc) check out the download page at the radare2 website.
Updating
As I said before, it is highly recommended to always use the newest version of r2 from the git repository. All you need to do to update your r2 version from the git is to execute:
$ ./sys/install.sh
And you’ll have the latest version from git. I usually update my version of radare2 in the morning, while watching cat videos.
Let’s use radare2 to reverse engineer a Gameboy ROM!
Check it out @ https://t.co/g1kYJuShzE@radareorg #radare2 pic.twitter.com/7FJOB3SdKS— Itay Cohen (@megabeets_) October 9, 2017
Playing with Gameboy ROM
This post will describe how I solved simple.gb, a Gameboy ROM challenge written by @condret. It was actually my first time reversing a Gameboy ROM — and it was awesome!
First thing I did was to open the binary in radare2 and check for its architecture and format:
| $ r2 simple.gb — For a full list of commands see `strings /dev/urandom` [0x00000100]> i~format format ningb [0x00000100]> i~machine machine Gameboy |
The
icommand gives us information about the binary. Checki?for more commands.Tilde (
~) is r2’s internal grep.
Surprise, surprise, it is a Gameboy ROM — dah. After reading a bit about its instruction set we should go to the mission.
The obvious thing to do is open the ROM in an Gameboy emulator. I downloaded the good old emulator I used back in the days when I played Pokemon: VisualBoy Advance.
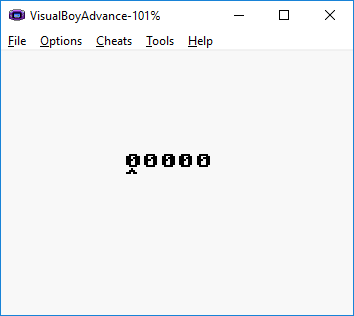
Let’s open the ROM in our emulator and see what we have:
Woops, wrong file. Bad habits… Let’s try again:
Cool! It’s a simple game where, by using the arrow keys, you increase/decrease 5 digits. We ‘simply’ need to find the correct password.