Description:
New Avenger | Stego 300 ptsThe Avengers are scouting for a new member. They have travelled all around the world, looking for suitable candidates for the new position.
Finally, they have found the perfect candidate. But, they are in a bad situation. They do not know who the guy is behind the mask.
Can you help the Avengers to uncover the identity of the person behind the mask ?
Megabeets$ binwalk avengers.gif DECIMAL HEX DESCRIPTION ------------------------------------------------------------------------------------------------------- 0 0x0 GIF image data, version 8"9a", 500 x 272 885278 0xD821E Zip archive data, at least v2.0 to extract, compressed size: 13422, uncompressed size: 13780, name: "1_image.jpg" 898769 0xDB6D1 Zip archive data, at least v1.0 to extract, compressed size: 1796904, uncompressed size: 1796904, name: "image_2.zip"
Yep, the gif file contains two more files within, lets unzip the image:
Megabeets$ unzip ./avengers.gif Archive: avengers.gif warning [avengers.gif]: 885278 extra bytes at beginning or within zipfile (attempting to process anyway) inflating: 1_image.jpg extracting: image_2.zip
Nice! We now have two more files: image_2.zip and 1_image.jpg. Now lets try to unzip image_2.zip.
Megabeets$ unzip ./image_2.zip Archive: image_2.zip [image_2.zip] 2_image.jpg password:
Oh-no, it requires a password. Lets have a look at 1_image.jpg.
Haha, funny image. Now I want to have a deeper look at this picture, I opened it in hex editor and found the password:
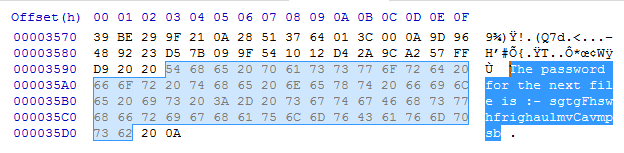
So the password is “sgtgFhswhfrighaulmvCavmpsb”, lets unzip the file:
Megabeets$ unzip ./image_2.zip Archive: image_2.zip [image_2.zip] 2_image.jpg password: <em>sgtgFhswhfrighaulmvCavmpsb</em> inflating: 2_image.jpg extracting: image_3.zip
Again?! We got 2 more files, and the password to the new zip was at the end of the new image, and the new zip contained another zip and an image. Well, I see where it going to, so I opened python and automate the process:
from zipfile import ZipFile
import string
# list storing the passwords, it might help
passwords =[]
i = 1
while True:
# read the last line of the file
f = reversed(open("%s_image.jpg"%i).readlines())
passw = f.next()
try:
# extract the password from the last line, if failed - it's the last zip.
passw = passw[passw.index(':- ')+3:passw.index(' \n')]
except:
break
# extract the zip file using the password
with ZipFile('image_%s.zip'%(i+1)) as zf:
zf.extractall(pwd=passw)
i+=1 # add the password to the list of passwords
passwords.append(passw)
Ta-dah! We extracted all the zip files and gםt 16 images and 15 passwords. This was the last image:

lol.
So now we have 15 passwords, each contains 26 characters:
sgtgFhswhfrighaulmvCavmpsb lppujmioEaynaqrctesAnztgib lrphntGpzjhkswskepnilrwwjm hmohAmgcomgpjjhLnqpkepuazi qjqxzuSkiyjzazwwsqchiqvgoQ ujinpqyghiulozjnyprZpnswnp tsquviQwxtgpgarlxelvakaOpo jljykvfZSycpvscqvzjwelKhok cqjausmhroogiuabcbpRmsyzpo qakrlxrGswfovmxhxpjzfyfrie jyxbLszctbveelbgxtilzfbQng heojthirkakqvvmxjgAWzuekcp nkpbhyUmiabnymvzmcppejiisy mIsmsmsmxpfvkolTbnkafkgvgx tsYinxviqeykguqznjscomgqbh
The password looks like garbage, it’s not Base64 or some known encoding. The first thing to pop up is the capital letter inside each password. Every password contains one or two capital letters. I know that the English alphabet contains 26 letters, so maybe I can map the location of each capital to the matching letter in the alphabet. i.e, if ‘F’ is in passw[4] i’ll take alphabet[4] which is ‘e’ and so on. I added this code to my script:
locations = []
for p in passwords:
for c in range(26):
if p[c] in string.uppercase:
locations.append(c)
map_result = ''
for l in locations:
map_result += string.lowercase[l]
print "Result: ", map_result
#Result: etitgepgztgxhiwthexstgbpc
I ran the script and got meaningless string: “etitgepgztgxhiwthexstgbpc”. Damn! I was so sure that the mapping is the solution, how can’t it be?! All the facts point towards mapping the alphabet. I decided not to give up and ran Caesar Cipher on the string:
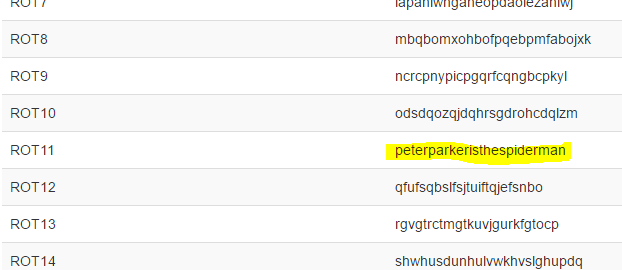
YAY! I was so happy to find Spidey is the new Avenger!
Here’s the full script:
The flag was: pragyanctf{peterparkeristhespiderman}





